This requires that the Splunk agent is getting the security event from the Domain Controller(s).
- Find the username of the person
- Log in to the Splunk server.
- Click on the Search button.
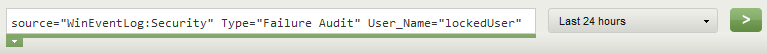
- Enter the search paramitters to find the user and select your time frame for the search:
source=”WinEventLog:Security” User_Name=”lockedUser”
- Then check the “Client_Address” field. This can be found on the left column.
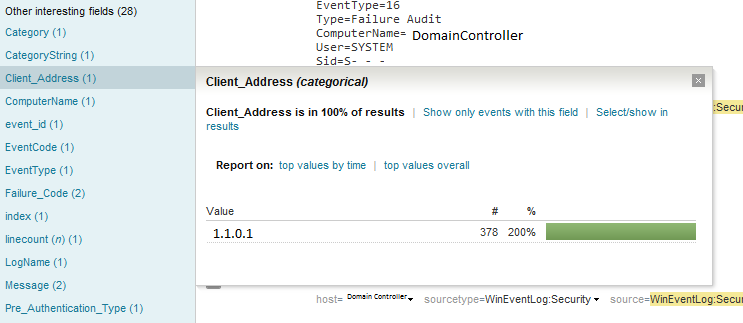
- The client IP shows where the lockout came from.
1. Find the username of the person
2. Log in to the Splunk server.
3. Click on the Search button
![]()
4. Enter the search paramitters to find the user and select your time frame for the search:
source=”WinEventLog:Security” Type=”Failure Audit” User_Name=”lockedUser”
![]()
5. Then check the “Client_Address” field. This can be found on the left column

6. The client IP shows where the lockout came from.